About the issue
The Yama Linux Security Module (LSM)
lets you to restrict the process trace (ptrace)
system call with the ptrace_scope parameter. Restricting ptrace reduces the risk of an attacker exploiting a compromised process to observe and control other processes on your system and steal sensitive information.
If Yama isn’t loaded on your system or if the ptrace_scope parameter is set to 0 (unrestricted), you might see an error message or experience unresponsive file pickers in 1Password for Linux when you try to:
- Import or export 1Password data (
.1puxor.csvfiles). - Upload or download SSH key files.
- Add, attach, or replace files when creating or editing items.
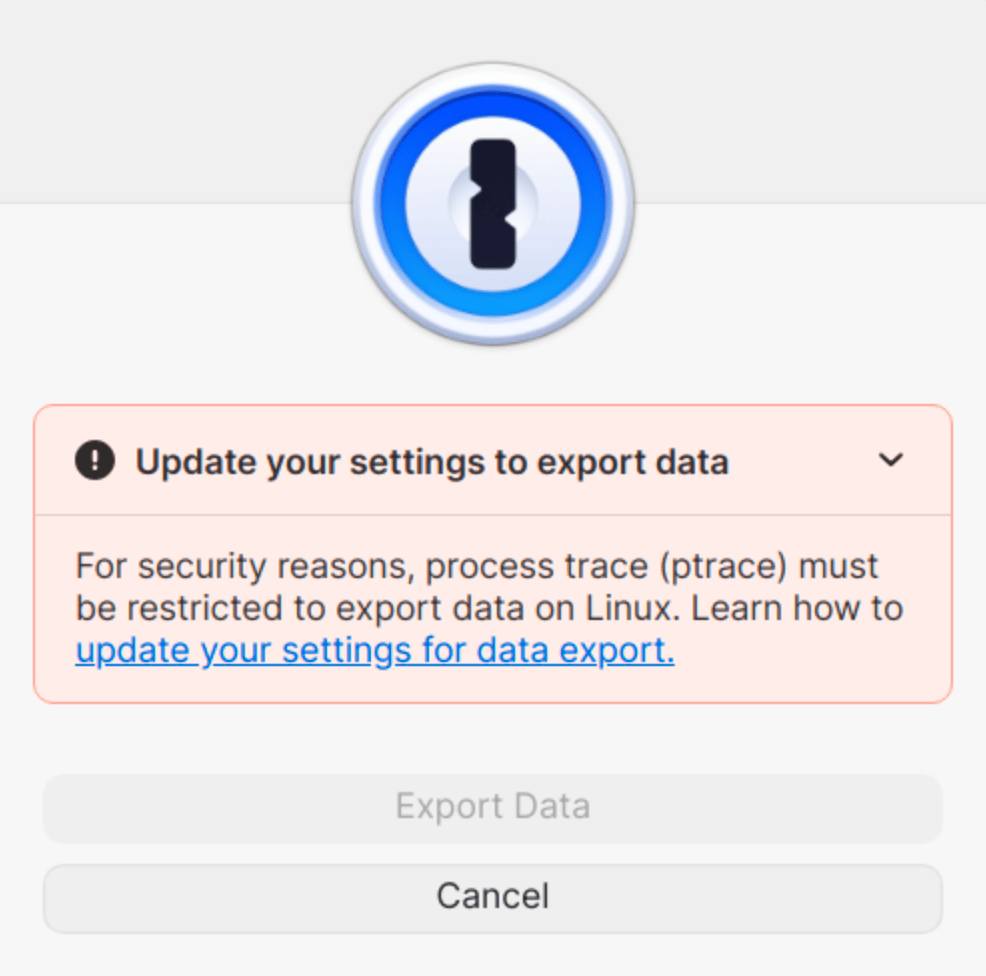
What you should do
Set Yama’s ptrace_scope parameter to 1 (restricted), so you can use 1Password for Linux to import and export 1Password data and other files.
Before you start:
Make sure you’re using 1Password for Linux 8.10.38 or later. Learn how to update 1Password.
Run the following command in the terminal to check if Yama is loaded and active (
ptraceis restricted) on your system:cat /proc/sys/kernel/yama/ptrace_scope- If Yama is loaded but not active, the displayed value will be
0. Follow the steps to setptracerestrictions. - If Yama isn’t loaded, you’ll see
No such file or directory. Follow the steps to load the Yama module on your system.
- If Yama is loaded but not active, the displayed value will be
If Yama is loaded
If you verified that Yama is loaded but not active, you’ll need to set the value of the ptrace_scope parameter to 1 (restricted).
Run one of the following commands in the terminal to restrict process trace:
Temporary: Run this command if you want the parameter setting to revert when you restart your computer.
sudo sysctl -w kernel.yama.ptrace_scope=1Permanent: Run this command if you want the parameter setting to persist when you restart your computer.
sudo sysctl -w kernel.yama.ptrace_scope=1 | sudo tee -a /etc/sysctl.conf
Restart 1Password.
Get help if you still can’t import or export your 1Password data or use file pickers in 1Password for Linux.
If Yama isn’t loaded
If you see No such file or directory when you check if Yama is loaded, you’ll need to add Yama to your bootloader’s user configuration file.
Help
These steps reference a configuration file for the GRUB 2 bootloader. If you use a different bootloader, or if these steps don’t match what you see on your system, refer to the documentation for your bootloader and Linux distribution.
Step 1: Verify your system’s active security modules
Run the following command in the terminal to check your system’s active security modules:
cat /sys/kernel/security/lsmTake note of the list that gets returned (you’ll need this list for step 3). For example:
lsm=landlock,lockdown,integrity,apparmor,bpf
Step 2: Locate the kernel command-line parameters in the bootloader’s user configuration file
Important
Back up your configuration file
Before you make any changes to the bootloader’s configuration, create a backup copy of the /etc/default/grub file and save it in another location.
Open the
/etc/default/grubsystem file in an editor with root permissions, like Nano. For example:sudo nano /etc/default/grubNavigate to the
GRUB_CMDLINE_LINUX_DEFAULT=line that contains kernel command-line parameters and locate the security module parameter: eithersecurity=moduleorlsm=module1,module2..., depending on your kernel version. For example:GRUB CMDLINE LINUX DEFAULT="quiet nosplash security=apparmor"GRUB CMDLINE LINUX DEFAULT="quiet nosplash lsm=landlock,lockdown,integrity,apparmor,bpf"
Step 3: Modify the security module parameter to add Yama
Add or update the LSM parameter in the GRUB CMDLINE LINUX DEFAULT= line to include Yama and any other active security modules.
Help
Where to add Yama in the list of security modules
The LSM parameter uses a comma-separated list to set the initialization order of Linux Security Modules at boot time. The default configuration order places Yama after minor modules like Landlock and Lockdown, and before major security modules like AppArmor, SELinux, Smack, and TOMOYO. For example: lsm=landlock,lockdown,yama,integrity,apparmor,bpf.
Your list may include different security modules. See the Linux kernel git repositories for more examples.
Use the list from step 1 to determine which security modules need to be included in the LSM parameter, and add Yama to that list. Then follow the steps for one of the options below, depending on what you see on the
GRUB CMDLINE LINUX DEFAULT=line:- If you see the
security=<module>parameter, remove it. Then add thelsm=parameter with the list of active security modules, including Yama (yama), in place ofsecurity=<module>. If there are other parameters on that line, make sure there’s a space between each parameter. - If you already see the
lsm=parameter on that line, check that all the active security modules are listed there, then add Yama (yama) to the list.
Do not change anything else on the
GRUB CMDLINE LINUX DEFAULT=line. There might be other kernel command-line parameters on that line that aren’t related to the security module parameter.When you’re done, the edited
GRUB CMDLINE LINUX DEFAULT=line might look something like this:GRUB CMDLINE LINUX DEFAULT="quiet nosplash lsm=landlock,lockdown,yama,integrity,apparmor,bpf"- If you see the
Save your changes to the
/etc/default/grubfile and exit the editor.
Step 4: Apply your changes to load Yama
Run the following command to apply the changes you made to the
/etc/default/grubfile:sudo grub2-mkconfig -o /boot/grub2/grub.cfgRestart your computer.
Run the
ptrace_scopecommand again:cat /proc/sys/kernel/yama/ptrace_scopeIf the returned value is
1, Yama is loaded and active. You should now be able to import and export 1Password data and other files.If the returned value is
0, Yama is loaded but not active. Follow the steps to setptracerestrictions.If you’re having trouble loading Yama, make sure you added Yama to the security module parameter of the bootloader configuration file and that you applied your changes. If you’re still having trouble, contact 1Password Support.
Get more help
If you still can’t import or export data or files
- Confirm Yama is loaded and the
ptrace_scopeparameter is set to1. If you set a permanent
ptrace_scopeparameter, restart your computer and try again.If you used the temporary
ptrace_scopesetting, restarting your computer will reset the parameter to0. Run the following command to set permanent restrictions (you can change this later):cat /proc/sys/kernel/yama/ptrace_scopeThen restart your computer and try again.
Contact 1Password Support
If you’re still having trouble:
- Create a diagnostics report on your computer.
- Email 1Password Support with a description of the problem and attach the diagnostics report that you created.
Learn more
- How to keep 1Password up to date
- Linux Security Module Usage
- Linux kernel’s command-line parameters
- security/Kconfig (Linux kernel git repositories)
Was this article helpful?
Glad to hear it! If you have anything you'd like to add, feel free to contact us.
Sorry to hear that. Please contact us if you'd like to provide more details.